When Cloudflare Isn't Cloudflare: Dissecting a Fake Validation Attack Hidden in a WordPress Theme
Acest articol este disponibil și înromână
• 3 minutes read
A malicious JavaScript hidden in a WordPress theme impersonated Cloudflare's bot verification to steal user data.
It started like most WordPress compromises do - with a theme update that no one double-checked. The site looked fine, the console was quiet, and traffic was normal. Except nothing was normal in Paradise. Letțs take a step back to how it all started
A few days ago, I get a phone call from a friend telling me that his website was randomly funnelling specific people to a "bot validation page" presenting what he'd describe as a Cloudflare anti-bot Captcha check.
I asked for a full website backup, and after digging through the files, I found a neat little trap hiding in a file that had no business being interesting, because nothing really interesting takes place in the /wp-content/themes/sugar/assets/js/jquery.sliphover.min.js file.
On the surface, it was a standard jQuery plugin, four kilobytes of legitimate code. But at the end - tucked neatly after a semicolon - sat another two kilobytes that didn't belong. A small, elegant, and thoroughly malicious script designed to impersonate Cloudflare's bot verification screen and get fancy malware campaigns from a website called traffipulse.com.
The setup
Attackers managed to inject a theme file through a vulnerable plugin, sneaking the malware into one of its JavaScript dependencies. They didn't bother to mess with the PHP logic - just injected a payload into a file that every page loaded. Smart move.
From there, the script ran quietly, checking if the visitor was "worth it."
It targeted Windows 10 users with modern browsers, skipping anyone who looked like a bot, crawler, or headless browser. It even ignored small screens - because what kind of legitimate user roams the web on a 320-pixel viewport?
The illusion of Cloudflare
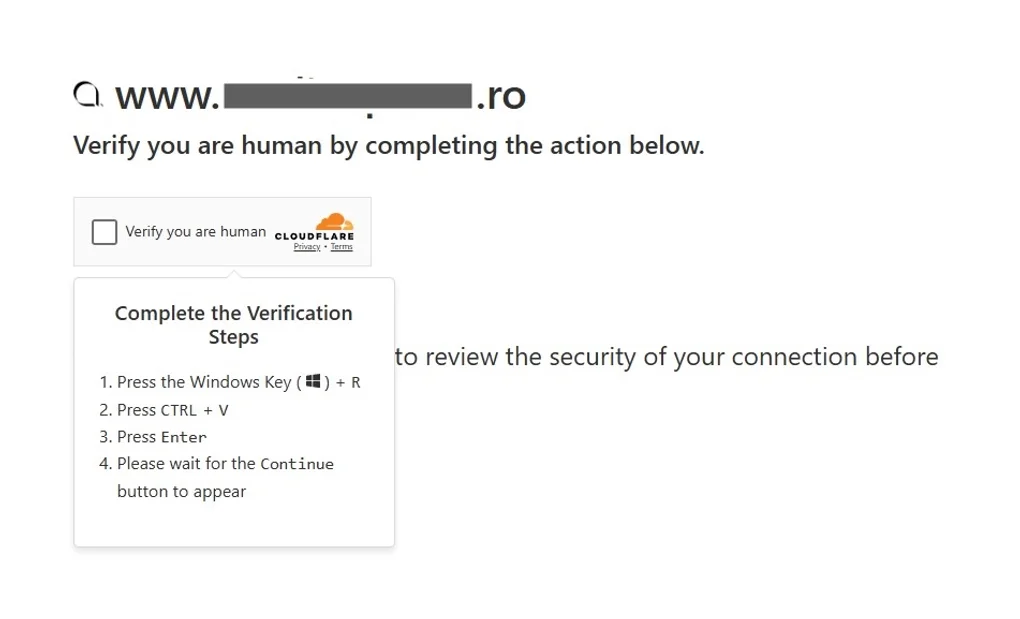
If you met its requirements, the code fetched a link from https://traffipulse.com/api/get, and presented a fake Cloudflare bot validation screen that instructs you to press a couple of keys to pass the test.
To make the ruse believable, it grabbed the site's favicon and domain, and displayed them in the fake validation screen. You'd think you were verifying your browser. In reality, you were entering commands on your computer without even realizing.
The craft behind the chaos
There's artistry in this kind of crime. The script avoided automated sandboxes with checks like navigator.webdriver and HeadlessChrome. It used localStorage to remember who'd already "passed" validation, so you wouldn't see the fake page twice. And it retried its network calls with increasing delays, the way only someone patient - or methodically evil - would.
Everything pointed to a campaign that knew what it was doing: hit humans, not bots, blend in, and stay quiet the rest of the time.
The social engineering layer
Visitors were shown a fake “Verify you are human” box that asked them to press Windows + R, paste a clipboard command, and hit Enter. The attackers were betting on trust: if the page looks official enough, users will comply. What actually happens next is that the copied command runs in PowerShell or mshta, fetching and executing a payload directly from the attacker’s infrastructure. It’s social engineering disguised as system maintenance, and the reason the malware only targeted Windows 10 with modern browsers is simple - those are the conditions that make the clipboard trick reliable.
Cleaning the mess
Removing it was the easy part:
- Identify and remove the malicious content from jquery.sliphover.min.js - don’t delete the whole file, as it will break the site’s functionality.
- Update all plugins, themes, and the WordPress core to the latest available versions. Change every possible password, because it’s better to be safe than sorry.
Why it matters
This wasn't a mass infection aiming to deface sites or spread ransomware. It was subtler - a supply-chain compromise buried in "cosmetic" files, weaponizing familiar files on the infrastructure to potentially infect users with infostealers.
The payload might be small, but hey, it's sophisticated enough to just work. Simple enough to fool anyone, polished enough to pass as real security measures.
The bigger picture
Malware like this reminds us that front-end JavaScript is part of your attack surface. Every plugin, every theme, every "free" asset someone uploaded five years ago can turn into an attack avenue.
If your security model stops at "I installed Wordfence once," you're missing the part where the front-end can steal your users before the server even notices.
The postmortem
One compromised theme, one malicious file, and one forgotten update were all it took. The malware's command server may go down tomorrow, but the infection vector - our collective laziness and complexity- will outlive it.


